Communications
Towards 6G Security: Technology Trends, Threats, and Solutions
Research on 6G is on the way
While we are witnessing the actively on-going deployment of 5G commercialization today, it is the very right time to start preparing for 6G, which will be a part of our lives in 2030 and beyond. To accelerate research for 6G, Samsung Research founded Advanced Communications Research Center back in 2019.
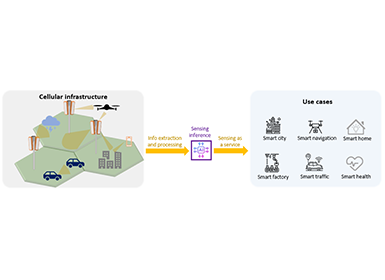
Many studies on 6G technology have indicated the following megatrends towards 6G: 1) network openness, 2) network AI (expansion of AI usage), and 3) massively connected machines/robots, as depicted in Fig. 1. [1].

Figure 1. 6G Megatrends.
On top of conventional performance requirements such as data rate and latency, which have been considered in the previous generations, trustworthiness is expected to be an essential requirement of 6G, and we have to develop 6G as the most secure mobile communication technology ever.
The technology trends towards 6G, including network openness, SW-based mobile communication system, virtualization/containerization, network AI, and quantum computing, directly affect security and privacy. Thus, new threats related to each technology trend should be investigated in advance to make 6G mobile communication secure.
6G Security Threats from Technology Trends
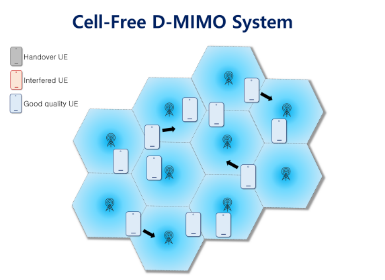
Major technology trends towards 6G are also expected to induce some security threats, and Fig. 2 highlights the expected security threats in 6G network. We will discuss some more details in the following.

Figure 2. The Landscape of Security Threats in 6G
Threats from Network Openness: As the number of low-performance devices such as drones, home appliances, and smart sensors is expected to explosively increase, system may become more vulnerable in an environment, where devices with low security reliability access mobile communication system
Threats from Open Source SW: The use of open source software will increase the attack surface. The number of vulnerabilities inherent in open source is increasing year by year, from 500 in 2008 to over 6,000 vulnerabilities in 2019. Since the source code is open, it is easy for an attacker to select an attack and analyze the target's operation. Particular open source SWs, which are not well maintained, may be even more vulnerable because patches are often poorly provided or incorrect patches are provided.
Threats from Network AI: By using the characteristics of training and interference of AI, attacker can intentionally fool AI model by entering deceptive data to make network system unstable, malfunctioning or unavailable, which is called Adversarial Machine Learning (AML) [2][3].
Privacy Threats: mobile network operators (MNOs) and external service providers are expected to analyze user information in various ways through data analytics and AI technologies to enhance quality-of-service (QoS) and quality-of-experience (QoE). However, personalization technologies in 6G open door for fine-grained privacy invasion. Thus, without reliable and secure environment, the use of user information may leak user information and cause serious threats to user privacy. [4]
Threats from Virtualization/Containerization: Virtualization and containerization are technologies that allow a single physical hardware (HW) resource to be divided into multiple logical resources as separate virtual machines (VMs) or containers where environments for running software services are isolated at the operating system (OS) level. By employing virtualization/containerization, operators have great advantages in terms of capital expenditure (CAPEX) and operating expenditure (OPEX). However, unless hypervisor, which manages VMs, or OS is securely managed, vulnerabilities can be easily spread over within all VMs or containers.
Threats from Introduction of Quantum Computing: Quantum computing (QC) can rapidly solve computationally very heavy problems such as the prime factorization of a very large number and the problem of discrete logarithms by utilizing quantum mechanical properties such as superposition and entanglement. Since QC is expected to be widely available in the 6G era, some of crypto algorithms will not be secure anymore.
Towards 6G Security: Solutions for Trustworthiness
Considering the increasing risk of security threats, we expect that trustworthiness will become one of the most important requirements in 6G. Potential solutions for trustworthiness provisioning is summarized in Table 1, and we explain some of them in the following.
Table 1. 6G Security: Trustworthiness Solutions for Various Security Threats.

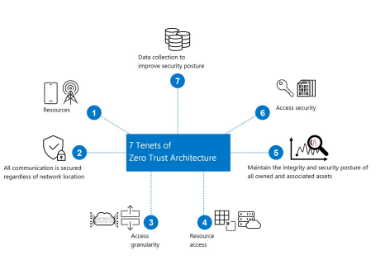
6G System Security Architecture for Openness: Since 6G is expected to become a more open network than 5G, the inside and outside of the network will become increasingly blurred. Therefore, the existing network security methods, such as IPsec, Firewall, intrusion detection system (IDS), etc., that apply security at the boundary point of the network will not be strong enough. To mitigate such limitation, the 6G security architecture should support the core security principle of zero trust (ZT) in the mobile communication network. ZT is a security paradigm that focuses on protecting system resources. ZT assumes that attacker can exist inside the network, and network infrastructure is accessible or untrusted from outside. Thus, it is necessary to continuously evaluate the trustworthiness against threats to internal assets, and apply protective measures to mitigate the risks. Zero trust architecture (ZTA) is a security architecture that utilizes the ZT concept and includes relationships between network entities (NEs), protocol procedures, and access policies as depicted in Fig. 3. Therefore, ZTA should be the core security principle in 6G security architecture [5].

Figure 3. Illustration of Zero Trust Concept.
Automated Management System for Open Source Security: The most important thing to tackle open source security problem is to embrace an automated management system throughout the development of 6G system, which manages vulnerabilities resulting from the use, update, and disposal of open sources. Thus, an automated management system to detect vulnerability and provide its patch is required to quickly check the threats. In addition, the secure over-the-air (OTA) procedure must be introduced to apply the patched software in a timely manner. Furthermore, it must be embraced a security governance system through a dedicated organization to manage 1) open source vulnerabilities from a long-term perspective, 2) changes in the perception of developers, and 3) introduction of security solutions.
Solution for Virtualization/Containerization Security: For various security issues of virtualization/containerization, systems must be operated only on a system equipped with secure virtualization layer including a security technology that detects hidden malicious codes such as rootkits. In addition, hypervisor must provide complete isolation of computation, storage, and network of different network functions with secure protocols such as transport layer security (TLS), secure shell (SSH), virtual private network (VPN), and so on. Furthermore, the hypervisor must be equipped with IDS/IPS/firewall to analyze the internal state of the VM and detect intrusion, called virtual machine introspection (VMI), which analyzes and detects security threats based on the vCPU register information, vMem data, file IO, and communication packets of each VM. In case of containerization, OS should properly configure the privilege of various containers, and prohibit the mounting of major system directories and direct exposure to the host device file container.
Privacy-preserving Solution: For the safe storage and use of user's personal information, mutually agreeable procedures should be defined throughout the collection, storage, use, and disposal of personal information between subscriber, MNO, and service provider. Through these procedures, the 6G system minimizes the collection of unnecessary personal information, keeps personal information safe on a trusted execution environment (TEE) and reliable SW, and minimizes or anonymizes exposed information when using personal information. When providing personal information, MNO must verify proper authenticity and authority. In addition, when using and analyzing user information, it can be anonymized to protect privacy or encrypted with homomorphic encryption (HE) to make the data available in an encrypted form. AI-based solution such as learning-based privacy-aware offloading scheme can be also utilized to protect both the user location privacy and the usage pattern privacy [6].
AI Security Technologies: To protect subscriber and mobile communication system from AML, transparency verifying how securely AI systems operate against AML must be ensured. First, AI models must be created in a reliable system. It is also required to embrace a procedure such as digital signature to check whether the AI models operating in user equipment (UE), radio access network (RAN), and core have been maliciously modified or altered by a malicious attack. If a malicious AI model is detected, a system must execute self-healing or recovery procedures. To support robust AI, system should also limit the data collection for AI training from only the trusted network elements [7].
Adoption of Post-Quantum Cryptography: 6G system should abolish existing asymmetric key encryption algorithms, which will become vulnerable with the introduction of quantum computing. Many researchers have been actively researching Post-Quantum Cryptography (PQC) solutions including lattice-based cryptography, code-based cryptography, multivariate polynomial cryptography, and hash-based signature. National Institute of Standards and Technology (NIST) of the US, which leads PQC research, is expected to select appropriate PQC algorithms between 2022 and 2024. The length of key currently being reviewed as candidates for PQC is expected to be several times longer than 1,000 bits of the existing Rivest–Shamir–Adleman (RSA) widely used in cryptosystem. The computational overhead of PQCs is expected to be greater than the existing RSA algorithm [8]. Therefore, it is necessary to properly introduce PQC with the 6G network HW/SW performance and service requirements.
To Make 6G Mobile Communication Secure
Samsung, along with other companies actively working on 6G security, will continue to work on all remaining aspects of the security issues. While intensively investigating new threats from trends, we have been developing new solutions to make 6G mobile communication completely secure. When 6G mobile communication is commercialized, we should be able to enjoy the most secure mobile communication ever.
Publication
https://ieeexplore.ieee.org/document/9579382
Reference
[1] “Samsung 6G White Paper: The Next Hyper-Connected Experience for All,” https://research.samsung.com/next-generation-communications, 2020.
[2] I. J. Goodfellow, J. Shlens, and C. Szegedy, “Explaining and Harnessing Adversarial Examples,” arXiv preprint arXiv:1412.6572, 2015.
[3] B. Biggio, I. Corona, D. Maiorca, B. Nelson, N. ˇ Srndi´c, P. Laskov, G. Giacinto, and F. Roli, “Evasion attacks against machine learning at test time,” in Joint European Conference on Machine Learning and Knowledge Discovery in Databases. Springer, 2013, pp. 387–402.
[4] H. D. Trinh, A. F. Gambin, L. Giupponi, M. Rossi, and P. Dini, “Mobile traffic classification through physical control channel fingerprinting: a deep learning approach,” IEEE Transactions on Network and Service Management, 2020.
[5] “Zero Trust Architecture,” https://csrc.nist.gov/publications/detail/sp/800-207/final, Accessed 11. 04, 2020.
[6] M. Min, X. Wan, L. Xiao, Y. Chen, M. Xia, D. Wu, and H. Dai, “Learning-based privacy-aware offloading for healthcare IoT with energy harvesting,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 4307–4316, 2018.
[7] M. Juuti, S. Szyller, S. Marchal, and N. Asokan, “Prada: Protecting against dnn model stealing attacks,” in IEEE European Symposium on Security and Privacy (EuroS&P), 2019, pp. 512–527.
[8] K. Basu, D. Soni, M. Nabeel, and R. Karri, “NIST Post-Quantum Cryptography-A Hardware Evaluation Study.” IACR Cryptol. ePrint Arch., vol. 2019, p. 47, 2019.