Communications
Zero Trust Architecture for 6G
Most of traditional security systems are perimeter-based approaches, in which the strategies are focused on protecting organization’s networks by securing its external boundaries with defensive barriers, such as firewalls, VPNs (Virtual Private Networks), and Demilitarized Zones (DMZs). However, as mobile communication systems become increasingly complex due to openness, driven by virtualized radio access network (RAN)/core network (CN) on public hardware (H/W)/cloud, traditional security models are no longer sufficient to defend against a variety of risks, e.g., lateral movement, insider attacks, or the compromise of trusted components. Therefore, many organizations are already moving toward Zero Trust Architecture (ZTA), which assumes no implicit trust and continuously verifies and authorizes users and devices, even inside the network. By minimizing trust by default and reducing the attack surface, ZTA ensures robust and dynamic protection in the next generation communication systems.
This article provides a comprehensive overview of ZTA and discussion of ZTA in cellular network. In addition, this article describes specific use cases of ZTA for 6G network.
2. Zero Trust Architecture
In perimeter-based models, systems are likely to fail to address malicious or negligent actions by employees or trusted users. Furthermore, if external attackers gain initial access authorization, they can exploit implicit trust within the internal network to access critical servers, databases, and storage devices. To overcome these limitations, ZTA has been introduced.
ZTA represents a modern cybersecurity framework that diverges from the traditional perimeter-based architecture. Unlike perimeter-based systems, which assume internal network components are inherently trustworthy, ZTA operates under the assumption that every user, device, and network flow can be potentially hostile or vulnerable. This shift in perspective aims to minimize risks such as breaches and lateral movement within the network by emphasizing continuous authentication, strict access control, dynamic policy enforcement, and thorough monitoring of assets. By segmenting resources and continuously verifying trust, organizations can significantly reduce their attack surface and better protect sensitive data, regardless of user location or network boundaries.
The National Institute of Standards and Technology (NIST) published the ZTA document of NIST SP 800-207 [1]. NIST defined the seven tenets, as the foundation of the Zero Trust (ZT) security model. Seven tenets overcome the limitations of traditional perimeter-based security approaches and provide core principles to effectively counter evolving threats. These principles enable organizations to build and operate ZT security frameworks tailored to their specific needs.
By adopting ZTA, organizations can significantly enhance their security posture. Continuous monitoring and validation of all network flows and user activities enable early detection of suspicious behavior, reducing the risk of breaches and lateral movement. Strict access control ensures that users and devices are granted only the minimum necessary permissions, minimizing the potential impact of compromised credentials or devices. Additionally, dynamic policy enforcement allows organizations to adapt security measures in real-time based on evolving threats and user contexts. This proactive approach not only strengthens the overall security infrastructure but also ensures resilience against sophisticated cyberattacks.
In summary, by leveraging ZTA principles, organizations can build robust security systems that continuously verify trust, enforce strict access controls, and adapt to emerging threats, ultimately safeguarding sensitive data and critical assets in an increasingly complex digital landscape including mobile network.
3. ZTA Status for Cellular Network
Mobile network operators increasingly recognize ZTA as a key pillar of their security strategies for 6G networks. This shift is driven by the evolving nature of future networks, characterized by openness, heterogeneity, cloud-native architecture, and multi-operator environments.. Traditional perimeter‑based defenses such as IPsec, TLS, and firewalls are no longer sufficient in these contexts, as 6G blurs the boundaries between trusted “inside” and untrusted “outside” domains. Operators therefore demand continuous verification, least privilege access, micro‑segmentation, and real‑time risk evaluation to mitigate both external intrusion and lateral movement by compromised entities within the network [2].
For telecom infrastructure to effectively implement ZTA, operators need tailored functional capabilities that extend beyond vendor offerings. These capabilities include comprehensive visibility and analytics across all network domains, automation and orchestration for policy enforcement, and robust governance aligned with The Cybersecurity and Infrastructure Security Agency (CISA) and NIST ZT maturity models. In response to these needs, standardization bodies such as 3GPP and O‑RAN (WG11) are developing telecom‑specific ZTA requirements. These efforts focus on integrating micro-perimeters, decentralized identity management systems, and AI-powered anomaly detection and mitigation mechanisms designed to support operator workflows and multi-tenant cloud environments [3, 4].
Verizon’s 2025 Data Breach Investigations Report (DBIR), which examined 22,052 incidents and 12,195 confirmed breaches between November 1, 2023 and October 31, 2024, highlights critical security trends relevant to telecom operators like Verizon itself. The report emphasizes the urgent need for ZTA in operational security. The persistence of credential abuse and unpatched edge devices implies that continuous authentication, device attestation, real‑time anomaly detection and mitigation, and automated patch orchestration must be embedded at all operational layers. Additionally, with third-party involvement accounting for 30% of breaches and ransomware involved in 44% of breaches, Verizon and its peers must strengthen supply chain security measures, enforce least-privilege access, and incorporate ZT compliance metrics into vendor management processes [5].
The 3GPP also understands the benefit of ZTA in CN and starts studying of ZTA since release 18. At first, release 18 TR 33.894 report investigates how Zero Trust Security principles can be effectively applied within 5G system, analyzing potential threats and proposing necessary security mechanisms to mitigate risks. Detailed evaluation of the seven tenets was conducted to identify the technical gaps between the tenets and the current 5GS as shown in Fig. 1 [6].
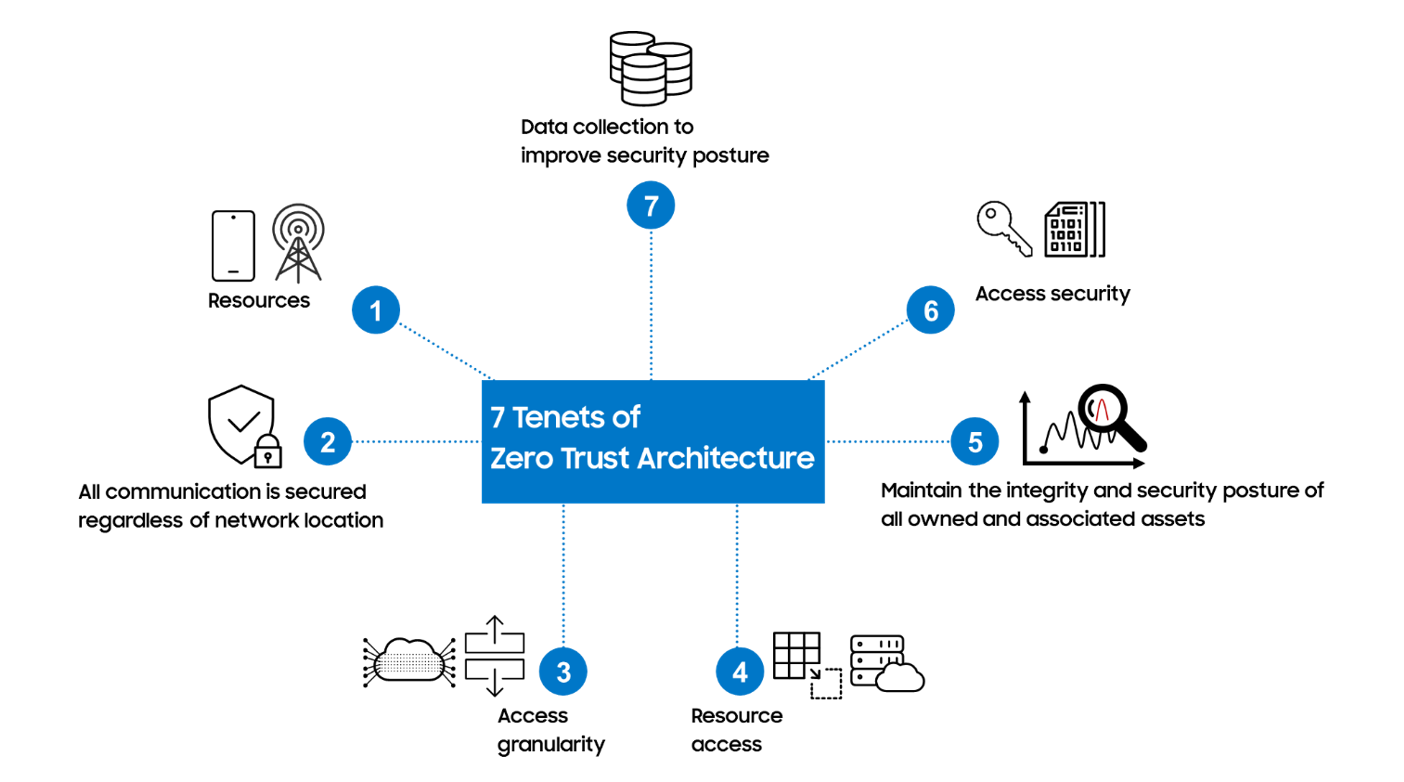
Figure 1. 7 Tenets of Zero Trust Architecture
As a results, 5GS addresses that the all data sources and computing are considered resources and their communications are secured regardless of network location. In addition, SBA security supports access granularity and access security between NF and NF and OAuth 2.0 in 5GS provides resource access. However, there are some gaps between 5GS and ZTA tenets. This report evaluates that security monitoring and trust measurement are under for further study. How the data from security monitoring is considered in access decisions is also for further study.
As a next study, the TR 33.794 report focuses on enablers for ZT Security in the 5G System, focusing on security analysis, recommendations, key issues, and potential requirements to achieve the following objectives [7]. One is data exposure for security evaluation and monitoring to identify potential threats and attack on the 5G SBA. The other is security mechanism for dynamic policy enforcement to detected threats and response capabilities in the 5G System.
This study outlines the two objective respectively. In data exposure perspective, data collection is essential for security evaluation and monitoring, including authentication failures, malformed messages, high service loads, and unexpected API usage. So, this study specifies general requirements for generating and protecting security event logs, ensuring confidentiality and integrity for both at-rest and in-transit logs, while addressing key issues related to data exposure and monitoring without introducing new interfaces or protocols.
In security mechanisms for policy enforcement perspective, 3GPP addresses normative work is needed to study how to enable ZT principle in 5G SBA. Specifically, following aspects are described as follows: NFs in the Service-Based Architecture (SBA) act as Policy Enforcement Points (PEPs) to enforce security policies and improve access control decisions based on security evaluation results. NFs, Network Repository Function (NRF), and Service Communication Proxy (SCP) can function as PEPs, taking actions such as blocking compromised NFs. On the other hand, SBA NF performs PEP functions with the Policy Decision Point (PDP) instructing these actions to the NF functioning as a PEP based on security incidents.
3GPP continues to study the gaps between ZTA principles and the current security architecture, consistently discussing methods to enhance the security of mobile communication systems.
4. Use case
A) Centralized Security Analysis for Continuous Monitoring
ZTA focuses on security analysis, recommendations, and potential requirements to enhance threat detection and response. To enable ZTA, a key challenge is determining how to effectively collect and analyze security-related data, highlighting the importance of identifying who and how this process should be managed.
The most effective approach to detecting security-related information in mobile communication systems involves the deployment of a centralized network entity (NE) capable of aggregating and analyzing security-related data comprehensively. However, in the 5G architecture, no dedicated NF for analyzing security event exists. The Network Data Analytics Function (NWDAF) performs little analysis of very limited security events. As a result, most operators rely on their own Security Information and Event Management (SIEM) systems, utilizing peripheral interfaces for independent analysis. This underscores the absence of interfaces for collecting security-related data, which hinders the ability to effectively gather and analyze such data for enhanced security measures
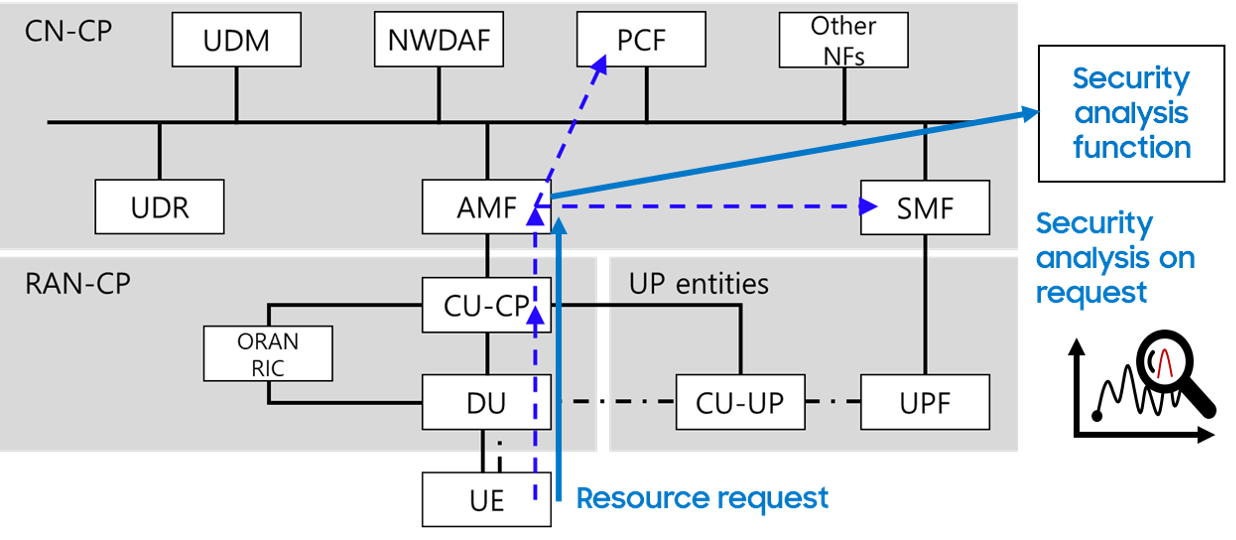
Figure 2. Centralized security monitoring and analysis under ZT principle
The introduction of a centralized NE for security analytics offers significant advantages in enhancing the security posture of mobile communication systems as shown in Fig. 2. A dedicated Security NE (called security analysis function) can request detailed security-related information from other NFs, including details about Network Elements (NE) and their behaviors. By aggregating and analyzing this data, the Security NE can identify vulnerable or malicious NEs, enabling proactive threat detection and mitigation. This centralized approach streamlines security management, improves threat visibility, and enhances the overall resilience of the network.
B) Abnormal RAN behavior Analysis
The evolution of mobile communication technologies has introduced significant security vulnerabilities due to increased openness and multi-vendor involvement. Current mobile communication systems involve contributions from multiple vendors, and the shift towards open architectures has led to the development of base stations, including specific software like xAPPs, by various vendors. These developments have expanded the attack surface, making the system more susceptible to prolonged and sophisticated attacks.
The virtualization and multi-vendor nature of vRAN introduce several security threats, creating challenges for operators deploying vRAN in multi-vendor or cloud environments to secure it in untrusted deployment environments due to their lack of visibility into these areas. This lack of visibility leaves vRAN vulnerable to various attacks, including snapshot attacks, side-channel attacks, hypervisor attacks, VM/container attacks, and bootloader attacks. These vulnerabilities can lead to the loss of confidentiality and integrity of both customer and operator data, posing significant risks to the overall security of the network as shown in Fig. 3.
Furthermore, a compromised RAN can serve as a bot for further attacks on other components of the network. Once infiltrated, attackers could exploit the compromised RAN to gain unauthorized access to the SBA, potentially leading to attacks on other NEs or resource theft. This escalation of threats highlights the interconnected nature of modern mobile communication systems, where a single compromised node can have far-reaching consequences across the entire network infrastructure like Advanced Persistent Threat (APT). Under the principles of ZTA, it is crucial to assume that RAN can be compromised and implement protective measures accordingly. Therefore, analyzing abnormal behaviors of RAN and applying appropriate mitigation strategies are essential for enhancing the resilience of mobile communication systems [7].
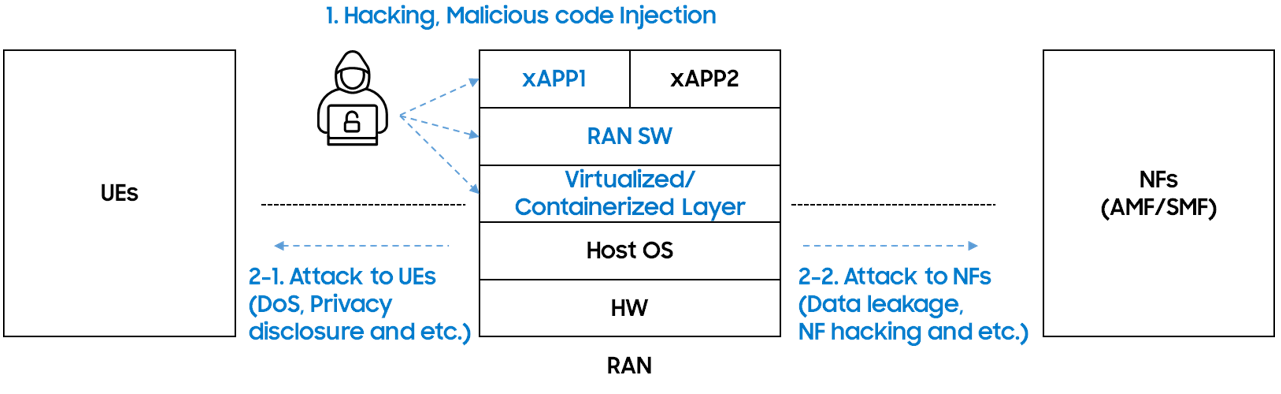
Figure 3. Attacks on vRAN/O-RAN
It is essential to move away from blindly trusting RAN behavior and focus on verifying abnormal activities. So, continuous monitoring of RAN activities like 'Periodic time,' 'Communication duration time,' 'Frequency of communication,' 'Traffic profiles,' and 'Suspicious message(s)' is critical to identify compromised RAN. By continuously monitoring RAN actions, potential suspicious behaviors such as 'gathering victims,' 'resource development,' 'DoS attacks,' 'unauthorized access,' 'manipulated RAN,' 'network sniffing,' 'sending malformed messages,' and 'malicious SW (vNF, cNF, NF, xAPP) installation' can be identified
By enabling the detection of abnormal RAN behavior, these proactive measures enhance overall system resilience, ensuring real-time threat identification and mitigation. This approach aligns with ZT principles, emphasizing continuous validation and adaptive security to maintain a secure and robust mobile network.
C) Dynamic Moving Target Defense (MTD)
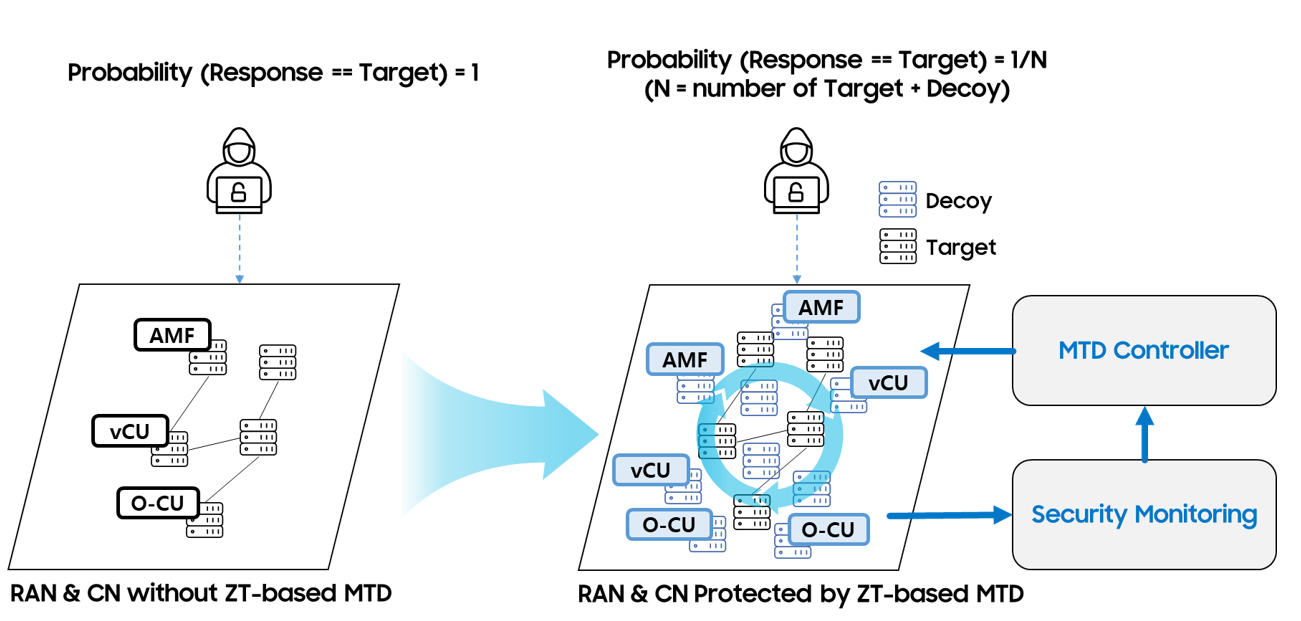
Figure 4. ZT-based MTD strategy for cloud-native RAN and CN protection
Moving Target Defense (MTD) is a proactive security technology that targets sophisticated attacks such as Advanced Persistent Threats (APTs) and zero-day. APTs infiltrate internal networks undetected, remain active for extended periods, and continuously steal assets, while zero-day attacks exploit previously undiscovered vulnerabilities. MTD increases the workload of attackers during the reconnaissance phase by making it more complex to identify targets. Additionally, even if an attack is executed against a specific target, MTD shifts the target to evade the attack, thereby increasing the overall complexity of the attack process. As shown in Fig. 4, MTD increases the complexity of an attack by reducing the probability of an attacker identifying a target to carry out an attack, such as by virtually expanding the topology of protected RAN and CN.
Applying ZT-based dynamic MTD security policies to next-generation communication systems can serve as a key technology to transition from static to dynamic/adaptive defense systems. This approach is expected to enhance security, ensure service continuity, and lay the foundation for future autonomous security systems. By designing a method for applying ZT-based dynamic MTD security policies, it is anticipated to establish a zero trust network security towards 6G.
Specifically, the following security effects are expected with ZT-based MTD:
1) Reduction of Attack Surface: By periodically changing critical resources such as communication paths, IP addresses, and port numbers between NFs, it becomes difficult for attackers to continuously detect and target specific points.
2) Improved APT and Zero-Day Attack Response: In fixed infrastructure environments, unknown vulnerabilities (Zero Day) and long-dormant APTs are effective. However, by introducing MTD, attackers are forced to continuously re-collect information, significantly reducing the likelihood of successful attacks.
3) Enhanced Service Availability: By bypassing or avoiding attacks targeting specific NFs or interfaces, such as Distributed Denial of Service (DDoS), and continuously changing network paths and access points, the risk of service interruption is minimized, strengthening service availability against attacks.
4) Neutralization of Targeting Attempts: By periodically changing the location and identification information of key NFs such as 5G Core's AMF, SMF, and UPF, it becomes difficult to identify specific targets, neutralizing targeted attacks.
5) Flexible Security Framework: By setting the scope and method of MTD application differently based on service characteristics, security threat levels, and user groups, a dynamic policy-based flexible security system can be provided.
6) AI-Based Autonomous Security System: When integrated with AI/ML-based security systems, MTD policies can be automatically adjusted based on real-time network threat analysis results, evolving into a core technology for AI-based situational awareness-driven autonomous security systems.
D) Remote Attestation Procedures (RATS) for shared COTS and Cloud Scenario
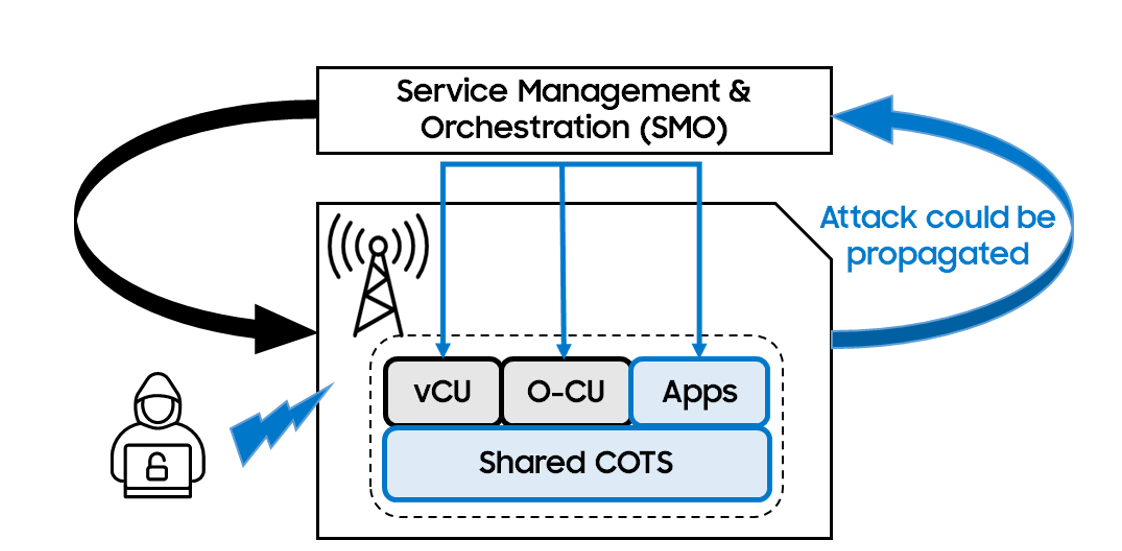
Figure 5. Illustration on how to trust vRAN S/W on shared H/W
As we move into the 5G and 6G era, RAN architectures are increasingly transitioning into cloud-native forms such as vRAN and O-RAN. While these architectures enhance flexibility and cost efficiency, they also introduce new challenges regarding trustworthiness and security.
In cloud-native environments, RAN components often run on shared infrastructure (multi-tenancy), meaning they may share physical servers or hypervisors with untrusted third-party applications. This creates a serious risk: a malicious application co-located on the same host could exploit vulnerabilities to interfere with or compromise the RAN functions, leading to security breaches such as privilege escalation, data leakage, or denial of service. As shown in Fig. 5, when third-party apps (untrusted) are compromised by an attacker and co-located with RAN S/Ws (e.g., vCU and O-CU) on a shared COTS server (multi-tenancy), attacks can be propagated to RAN S/Ws through the compromised third-party app.
To mitigate these risks, mechanisms are needed to verify the integrity and trustworthiness of RAN components, ensuring continuous verification before granting access or executing operations. A key part of the mechanism is attestation, which refers to a process where each NF proves its operational integrity, typically using cryptographic techniques. The cryptographic techniques include secure boot, Trusted Platform Module (TPMs), or Remote ATestation procedureS (RATS) [8] .
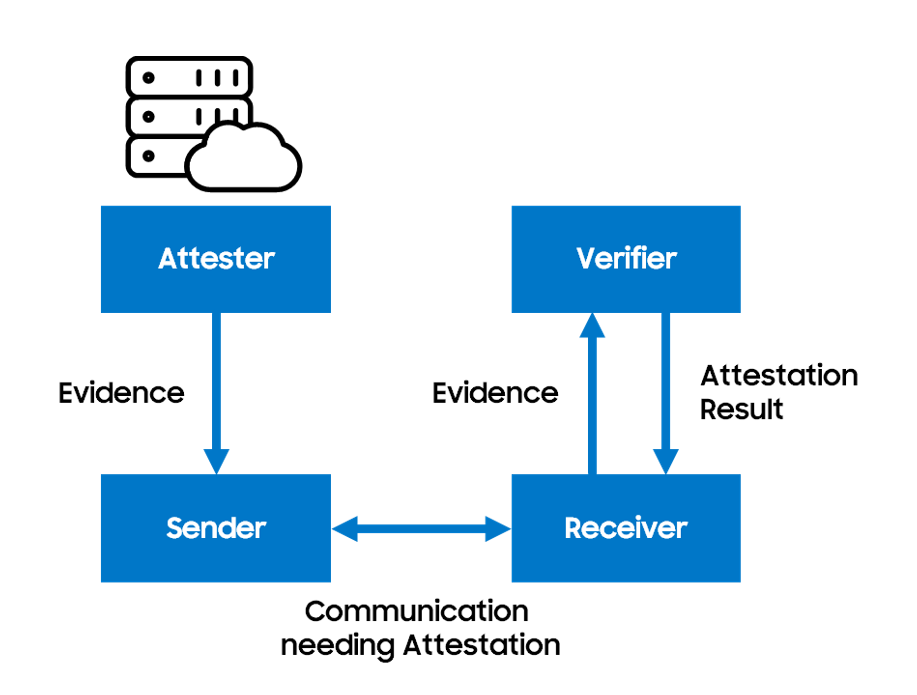
Figure 6. Concept of RATS
Among them, RATS allows a RAN node to cryptographically prove its current platform state (e.g., bootloader, kernel, runtime binaries) to a remote verifier before being allowed to operate. RATS ensures that vRAN/SWs, especially those in the cloud, are running approved software in secure configurations. Fig. 6 describe the detail procedures of RATS. RATS allows one system (attester) to produce believable evidence about its state. A remote peer (receiver) uses this evidence to decide whether the attester can be trusted. Hence, Using the attestation process, operators can verify whether systems and their components are working as expected on remote COTS or Cloud platform. RATS can support management-level remediation and resilience for operators immediately when issues arise.
The benefits include:
In conclusion, to ensure secure and trustworthy cloud-native RAN, especially in multi-tenant deployments, it is essential to adopt technologies like Remote Attestation backed by H/W-based roots of trust.
5. Challenges, Future works
As mobile communication systems evolve based on ZTA principles and incorporate continuous monitoring and evaluation, the security of the 6G system is significantly enhanced. This involves collecting and analyzing data from the SBA and AS layers, such as authentication failures, malformed messages, high service loads, and abnormal call flows, to detect potential threats. Additionally, security event logs must be generated, protected in transit and at rest, and used to identify compromised NEs or their suspicious activities. However, achieving ZTA in mobile networks requires further efforts, including efficient monitoring of vast amounts of data, optimizing network resource usage for analyzing suspicious data, and accurately identifying security threats.
6. Conclusion
The introduction of ZTA principles, such as data collection, continuous monitoring, and validation, will enable more effective analysis of security threats in mobile communication systems, significantly enhancing their overall security. By leveraging these advanced mechanisms, ZTA will contribute to building a more resilient and secure infrastructure for mobile networks in 6G.
References
[1] NIST Special Publication 800-207 Zero Trust Architecture
[2] NGMN 6G Requirements and Design Consideration, 02-2023
[3] NIST Advanced Security Architecture for Next Generation Wireless,04-2025
[4] Zero Trust Architecture for Secure O-RAN, O-RAN WG11, 05-2024
[5] Data Breach Investigations Report (DBIR), Verizon, 2025
[6] 3GPP TR 33.894 Study on applicability of the zero trust security principles in mobile networks
[7] 3GPP TR 33.794 Study on enablers for zero trust security
[8] 3GPP TR 33.848 Study on security impacts of virtualisation