Security & Privacy
Towards Next-Gen Authentication: Context-adaptive Behavior-based Device Unlocking
Motivation of On-Device Transparent Person Authentication
These days, users may interact with their smartphones up to several hundred times per day: to check emails, for messaging, watching YouTube, or playing games. This requires frequent and safe device unlock. Typically, PIN, fingerprint, and facial recognition are used. Despite strong security guarantees, these methods may be inconvenient in situations, where a user interacts with the device while doing other activities (walking, shopping, commuting oth.). Additional actions from the user side, such as password typing or swiping a fingerprint sensor in these conditions are not convenient. Some form of non-intrusive authentication would be preferable.
One possible solution would be to apply a form of continuous authentication based on behavioral patterns: a flow of information about a specific way of using the device. The fact that people use phones frequently around the day, gives a background assumption, that every phone user provides a steady and rich flow of such information. One obstacle is intensive CPU utilization, which is required to achieve high authentication accuracy and robustness against presentation attacks (spoofing). Thus, an innovative method for spoofing-resistant transparent user-friendly authentication with high accuracy and low CPU/RAM footprint is required.
Samsung R&D Institute Ukraine team made research in this area and presented the results in EURASIP Journal on Information Security. We suggested a technology for transparent on-device user authentication on smartphones.
State-of-the-art Solution for Behavior-Based Authentication
RSA SecurID, NuData Security, Touch ID, Face ID, and SecureAuth are examples of commercial access control systems (ACS) for mobile devices. They can be divided into several groups depending on the type of information used for authentication, as shown in the following diagram.

Figure 1. Landscape of authentication solutions for mobile devices. Proposed solution belongs to domain marked with dashed red line
ACSs for mobile devices are based on matching against something that the user knows (a password or a passphrase), possesses (a token), or is (biometrics and behavioral templates). The majority of modern solutions for on-device user authentication, including HYPR, SecureAuth, NuData, and TwoSense.AI, rely on biometrics or behavioral pattern collected from various sensors (fingerprint, iris, heartbeat, bioacoustics oth.). These solutions also utilize advanced methods for the reliable extraction of essential features from noisy streams of sensor data in varying usage contexts. ACSs are applied in various B2B and B2C scenarios. For example, NuData is a part of MasterCard's portfolio for personal authentication during financial transactions on mobile devices. Another example is TwoSense.AI which is an authentication service provider for both commercial and government companies.
The following table compares various commercial solutions for on-device user authentication.
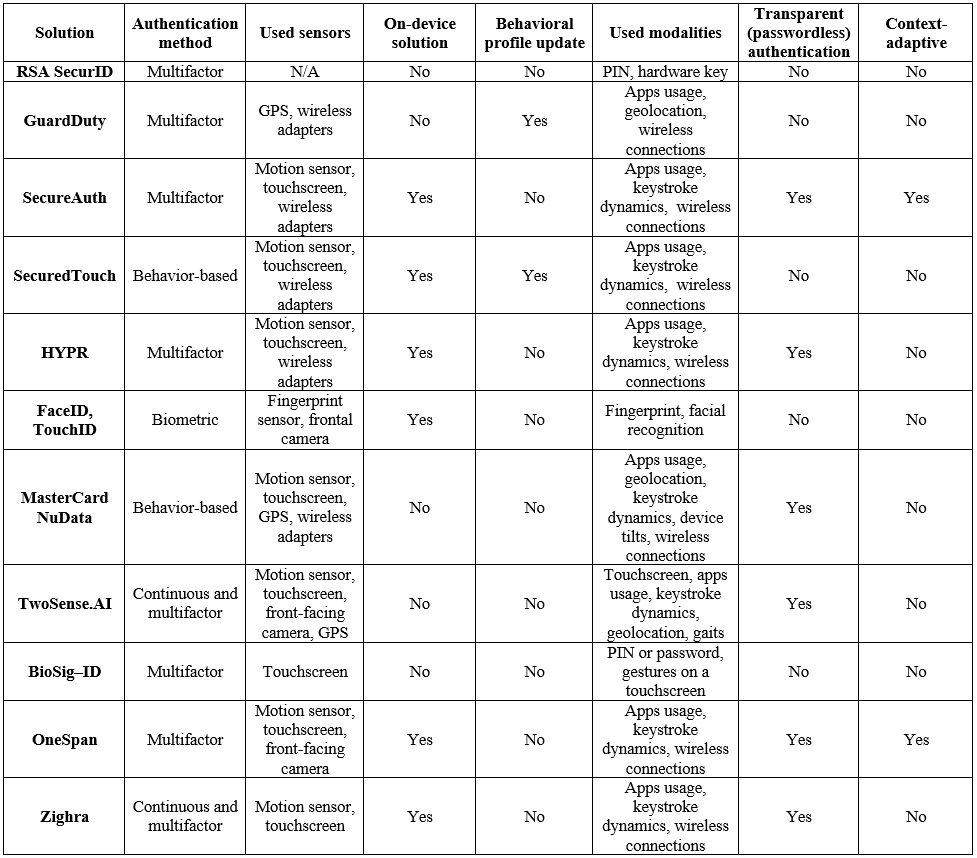
Table 1. Comparison of state-of-the-art commercial solutions in the domain of behavior-based user authentication on mobile devices
Many modern solutions for user authentication use a combination of authentication factors. Combining several modalities, such as keystroke dynamics, person-specific gestures, geolocation, and app usage patterns, allows constructing of a strong authentication mechanism from several "weak" factors. However, the accuracy of this approach highly depends on the usage context and the user’s physical activity. For example, drastic changes in fingerprint templates or keystroke dynamics, collected during the user still sitting and running, may lead to inappropriate growth of false negatives. Because of that, advanced solutions like OneSpan include context information in their authentication process. While this approach is possible, it raises privacy concerns, because contextual data may include sensitive things like user location or physical activities that expose health, gender, or other identifiers. Also, reliable context-aware authentication may require continuous monitoring, which drains the battery.
BehaviorID solution, presented in the paper, strives to address these challenges by providing a short-time user-adaptive multimodal context-dependent behavior-based privacy-preserving authentication method for use on smartphones.
BehaviorID: Key Features
The distinguishing feature of BehaviorID is the use of novel Adaptive Recurrent Neural Networks (A-RNN) to extract and track multiple behavioral templates with minimal computational overhead (Fig. 2).

Figure 2. User authentication procedure with proposed BehaviorID method
The BehaviorID technology is based on gathering signals from the device’s embedded sensors during short time intervals, namely between triggering events such as launching a predefined application and typing start. The gathered signals are combined into modality groups for further processing. For example, touchscreen keyboard timings and touch locations are grouped into "type patterns". Next, these modalities are used to recognize usage context and to select the appropriate settings for the A-RNN model. Then, each modality is processed by A-RNN to extract user-specific behavioral templates. Then the outputs of each A-RNN are processed with a decision-making module. In case of a positive decision (the user has been successfully authenticated), extracted features are used to update the A-RNN parameters, thus giving the system the ability to mitigate the behavioral pattern drift effect.
Note the ability of the A-RNN model to simultaneously track alterations of multiple behavior templates at a fixed (minimal) overhead. This feature allows for a significant reduction of the computational complexity for the whole authentication pipeline (excluding the use of additional modules for templates update). This makes A-RNN a preferable choice for resource-constrained smartphones: it allows to strengthen of the existing authentication methods with additional modalities at a fixed computational complexity. Here are several examples:
• Authentication by Face spoofing is the issue. Standard ways to thwart spoofing attacks include liveness detection, hi-tech
matching algorithms, or additional sensors. BehaviorID may help by analyzing small motions during authentication. If the
motion pattern differs from the one previously learned (or motion is absent), the device is kept locked.
• Password-based authentication. The issue is with weak passwords. It may be addressed in traditional ways (timeouts,
limited attempts count) or by utilizing behavioral approach: keystroke dynamics, device's small motions, keyboard hit map
oth. If the way how the user actually types the password differs from the previously-learned habit, the device will remain
locked regardless
of the correctness of the password.
• Continuous authentication - the system checks the user's presence transparently and continuously in the background
(without explicit authentication requests). Then this "trust chain" is used when, say, a banking app. is launched. The
challenge here is the battery drain, because continuous tracking may require keeping CPU awake. BehaviorID provides a
method to make measurements in CPU & in battery - efficient manner.
The following section provides BehaviorID comparison with known alternatives and gives evaluation metrics.
Real Cases Performance
During the evaluation, we considered several state-of-the-art solutions for behavior-based user authentication on smartphones, such as Abuhamad et al. ( https://ieeexplore.ieee.org/document/9007368), Reisinger et al. ( https://www.mdpi.com/2076-3417/11/24/11756 ), and MMAuth method (https://ieeexplore.ieee.org/document/9737094). The first one is based on modeling the dependencies between samples of behavioral templates using LSTM networks. The second method proposed by Reisinger et al. learns the features directly from gathered signals using the Unsupervised Learning approach. The third MMAuth method integrates the heterogeneous information about the user's identity from multiple modalities using an ad-hoc Deep Learning-based one-class classifier.
Performance evaluation was done using a set of public and in-house datasets of behavioral patterns for mentioned modalities in various usage contexts. The following datasets were used:
• The ExtraSensory dataset (http://dx.doi.org/10.1109/MPRV.2017.3971131) – includes measurements of several sensors for
60 persons on smartphones and tablets made “in the wild”. The data was captured by motion sensor, geolocation and
magnetometer for 15 smartphone models (Android and iOS).
• The MotionSense dataset (http://dx.doi.org/10.1145/3302505.3310068) – includes time series generated by motion sensor
of iPhone 6s smartphone. The device was kept in participant’s front pocket. The dataset includes estimation for 24
participants performed 6 physical activities (15 trials-per-activity in average).
• The SherLock dataset (http://dx.doi.org/10.1145/2996758.2996764) – is huge dataset of long-term tracking of smartphone
sensors with a high temporal resolution. The dataset offers explicit labels that capture the activity of applications running
on the device. It contains about 10 billion data records from 30 users collected over a period of 2 years and an additional 20
users for 10 months (totally 50 users).
• The H-MOG dataset (http://dx.doi.org/10.1109/TIFS.2015.2506542) – includes results of large-scale user study to collect
a wide range of behavioral patterns related to touch dynamics, gesture as well as movement and orientation of the phone.
The data of 100 volunteers was collected during sitting and walking.
• The UMDAA-02 dataset (http://dx.doi.org/10.1109/BTAS.2016.7791155) – consists of 141.14 GB of smartphone sensor signals
collected from 48 volunteers on Nexus 5 devices over two months. The data was gathered by frontal-facing camera,
touchscreen, motion sensor, magnetometer, light sensor, GPS, Bluetooth, WiFi, proximity sensor, temperature sensor and
pressure sensor. The data collection application also stored the timing of screen lock and unlock events, start and end
timestamps of calls, foreground application etc.
• The BB-MAS dataset (http://dx.doi.org/10.48550/arXiv.1912.02736) – is collected by international research teams for
analysis of the behavioral biometrics, obtained from multiple devices. Data from 117 subjects was collected for typing fixed
and free text, walking and touchscreen utilization on desktops, tablets and smartphones.
• Fixed-context dataset – was collected by our team during analysis of behavior-based authentication systems. The signals
were gathered for 30 users (at least 5 authentication probes per user) during still-standing. The users were requested to
enter a 10-characters passwords by left, right or both hands.
Usage of several datasets during performance analysis is caused by the absence of a single “universal” dataset for evaluation of behavior-based authentication systems for both short and long-term changes of users behavioral patterns. Thus, we divided considered datasets into two groups, namely with short-time (ExtraSensory, MotionSense and in-house databases) and long-term (SherLock, H-MOG and UMDAA-02 datasets) estimations.
Comparative analysis of state-of-the-art and proposed BehaviorID solutions was done for widespread usage scenarios. Spoofing Acceptance Rate (SAR) evaluation was done. Multimodal authentication in various usage contexts as well as long-term tracking of behavioral pattern alterations were performed. Our BehaviorID technology provides a similar performance or outperforms them in all considered cases:
• noticeable decrease of SAR (down to 9%) and False Rejection Rate (down to two times) values were obtained for the fixed
usage context;
• BehaviorID allows for reducing error rates up to three times in comparison with Abuhamad’s solutions for the case of
multimodal authentication in several usage contexts;
• in the most difficult case of long-term tracking of the behavioral template, BehaviorID outperforms Abuhamad et al. and
MMAuth solutions up to four times in terms of False Acceptance Rate while preserving fixed (low) computational
complexity
Please note that obtained results correspond to performance of considered solutions in different use cases and usage contexts, namely for fixed usage context (text typing during still standing), for a several usage contexts (during still standing, walking) and for tracking of long-term changes of behavioral patterns. Differences in the metrics can be explained by the fact that several datasets are used for evaluation. This is caused by absence in public domain a dataset that could be used for all considered cases.
Conclusion
We presented BehaviorID - a novel technology for on-device context-dependent, privacy-preserving, behavior-based continuous authentication. The BehaviorID is based on a computationally efficient A-RNN model for simultaneous tracking of ensembles of behavioral features collected from mobile phone built-in sensors. This allows for battery-friendly processing and fast adaptation of behavioral templates to alterations of user habits and changes in the user's physical state. Because of good accuracy vs. footprint balance, BehaviorID is suitable for a range of applications in authentication scenarios on embedded devices.
References
Published paper: https://jis-eurasipjournals.springeropen.com/articles/10.1186/s13635-022-00132-x





