Security & Privacy
Samsung's Secure Channel Protocol Libraries for Secure Element Infrastructure
Introduction
The Samsung R&D Institute Ukraine team has published implementations of the Secure Element (SE) [1], SCP03 [2], and SCP11 [3] communication protocols as OpenSCP-Java [4] and OpenSCP-Python [5] open-source libraries. It adheres to the latest Global Platform Secure Channel Protocol [6][7] specifications (SCP03 and SCP11) and makes it easier for Samsung partners to work with the technology in a compliant and interoperable manner. This blog post aims to introduce our contribution, provide typical applications for interested partners, and offer an essential technical overview. We also invite open-source contributors.
Secure Element in consumer devices. Why is it required
Embedded Secure Element (eSE) is a dedicated chip typically certified as an Evaluation Assurance Level (EAL) [8] 5+/6+ solution, which means the security level is sufficient to be used for operating with finances, mobile documents, and government-provisioned PII. eSE is a separate computing unit connected to the main Application Processor (AP) with a wired connection on the consumer device’s printed circuit board (PCB). Figure 1 gives a comparison of the eSE assurance level in relation to other security systems of various EAL levels.
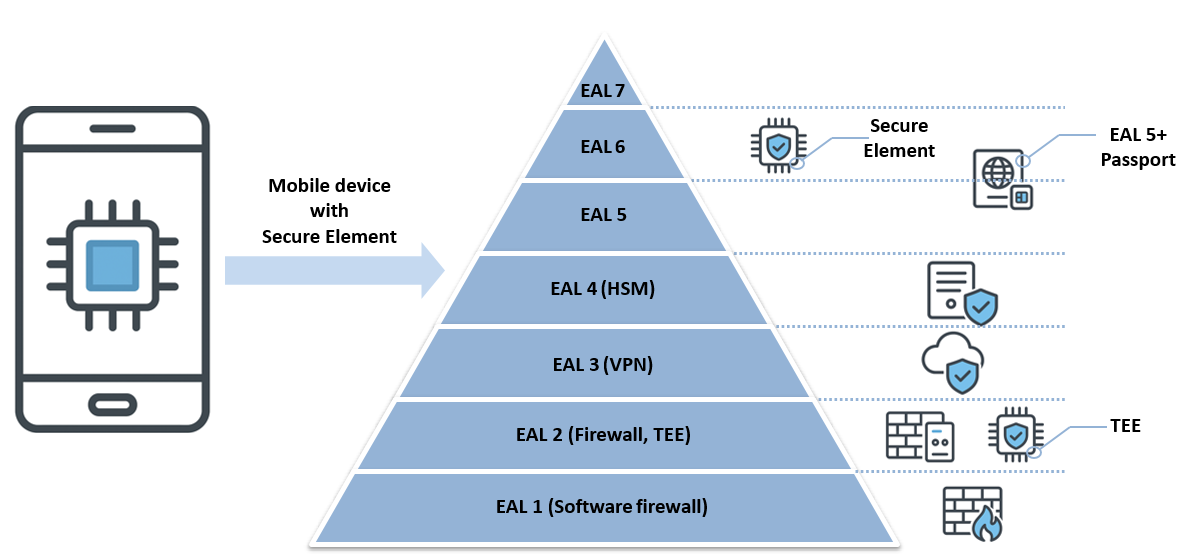
Figure 1. Evaluation Assurance Levels overview
eSE used in consumer electronics is often mandated by legislation requirements related to the minimum allowed security level, which is formally tracked by certifications. Certification requirements usually imply mandatory use of a Secure Area for processing and/or storing sensitive data in the certification target. As long as EAL5+/EAL6 security level is needed, eSE (or a similar hardware solution, like Knox Vault) becomes mandatory.
Standardization in the Secure Element tech area
Two major standardization organizations cover most areas related to the Secure Element:
The most referred document is ISO/IEC 7816-4:2020 [11], which explains command-response interfaces and related data for communication with the Secure Element.
Our open-source libraries OpenSCP-Java [4] and OpenSCP-Python [5] implement the latest amendments to GP Card Specification [9], which standardize Secure Channel Protocol (SCP) [7] approaches for trusted communication with Secure Element's domains (nested groups of SE applications with shared security policies living in a common execution environment). The specification includes several SCP protocols.
Our libraries implement two most widely-used protocols – SCP03 and SCP11:
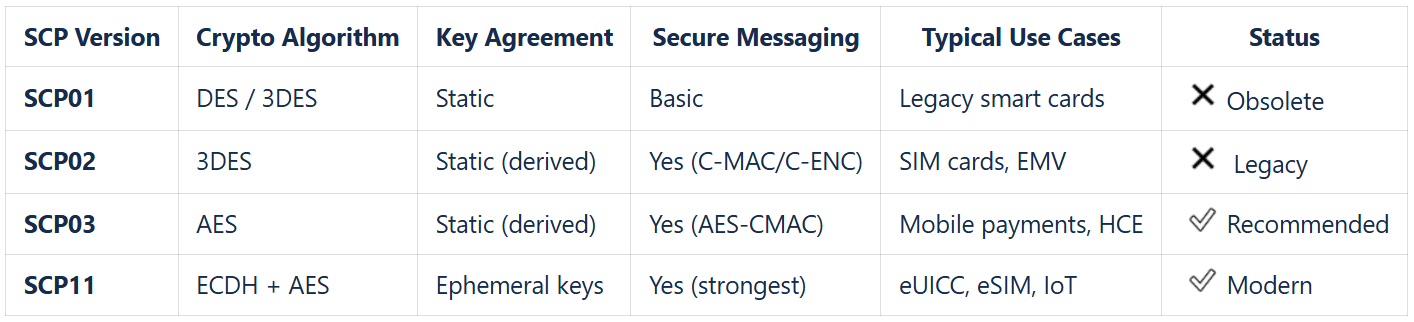
Table 1. SCP versions comparison
Samsung OpenSCP - motivation and features overview
Samsung has a lot of partners working with infrastructure, applications, and the Secure Element operating system. For them it is complicated to create an environment to build and test Secure Element features. Thus, the major motivation was to address these challenges to encourage partners involvement and enrich Samsung eSE ecosystem. Mobile Experience Security team decided to provide libraries, packages, API, and examples that cover the latest specifications to make eSE integration easier.
Our OpenSCP project is a standalone library that supports the latest SCP03 v1.2 and SCP11 v1.4 secure transport protocols in all operation modes. It consists of two open-source repositories:
Both Java and Python versions cover the specification equally.
The client application provides an unprotected communication between the host and the Secure Element, then OpenSCP wraps it with secure tunnel to protect against alteration, eavesdropping, replay, and other attacks. Mutual authentication of communication peers is provided. It helps to thwart attacks against Secure Element (when it is integrated into a compromised host to extract sensitive data, for example, for SE cloning) and attacks where SE chip is replaced with another compromised chip on the PCB (to mimic legitimate Secure Area). Secure Element has higher security level than the host where it is integrated. This means that sensitive data (like authentication credentials) cannot leave SE and get into consumer device's memory. So, encryption keys, digital signature private keys and other sensitive crypto material is generated, stored and used inside SE.
OpenSCP library aids at applying proper SCP communication protocol in specification-compliant way. OpenSCP makes it easier to adopt SCP to partner's specific threat model, use-cases and constraints. Also, the partner will benefit from community-provided patches. Here is short overview of commercial use of SCP03 protocol (symmetric crypto) and SCP11 (asymmetric crypto).
SCP03
SCP03 protocol can be used at manufacture time for credentials provisioning where SE and Device Keys Management server share AES key. Example is using SE for storing bank card credentials. Other examples are MNO provisioning to eSIM and SE domains/applets remote management. Major limitation is that an initial pre-shared master key is required, which is Ok for the factory, but may be impossible for the cases where the peers "meet for the first time". Here are the main features of SCP03:
Figure 2 gives an example of typical SCP03 setup to manage SE through Application/Device Vendor infrastructure.
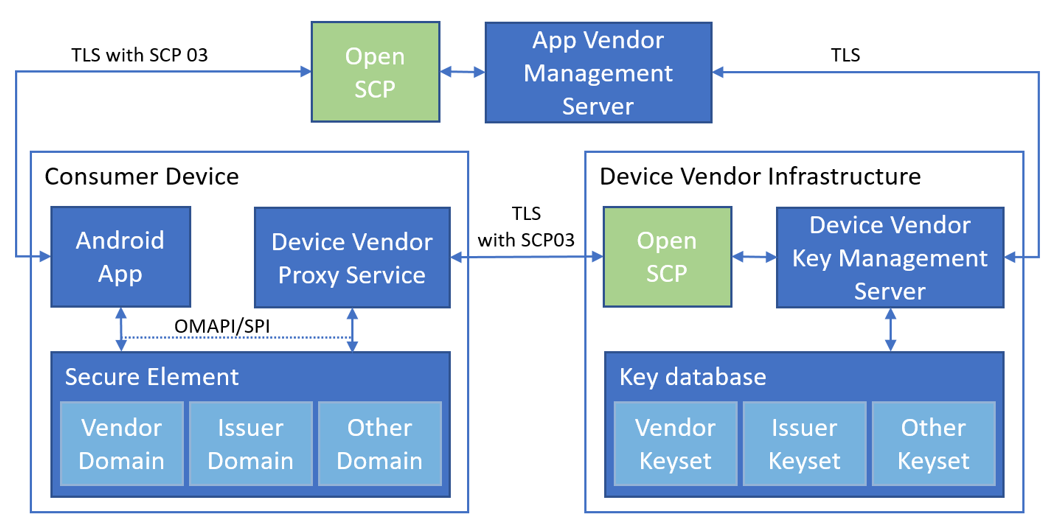
Figure 2. typical setup of SCP03
Symmetric key sets for SCP03 are usually intended for Secure Element’s domains and SE applications (applets) management. Secure Element usually has domains issued by the Device Vendor and other domains with a keyset available for the Application Vendor and its Android application. Figure 2 and Figure 3 explain the use of Samsung OpenSCP [4][5] for Application and Device Vendor servers, i.e. installing a new applet to SE. Similarly other operations can be implemented: deleting and updating applets, secure management of sensitive data inside installed applets, attestation and crypto keys provisioning.
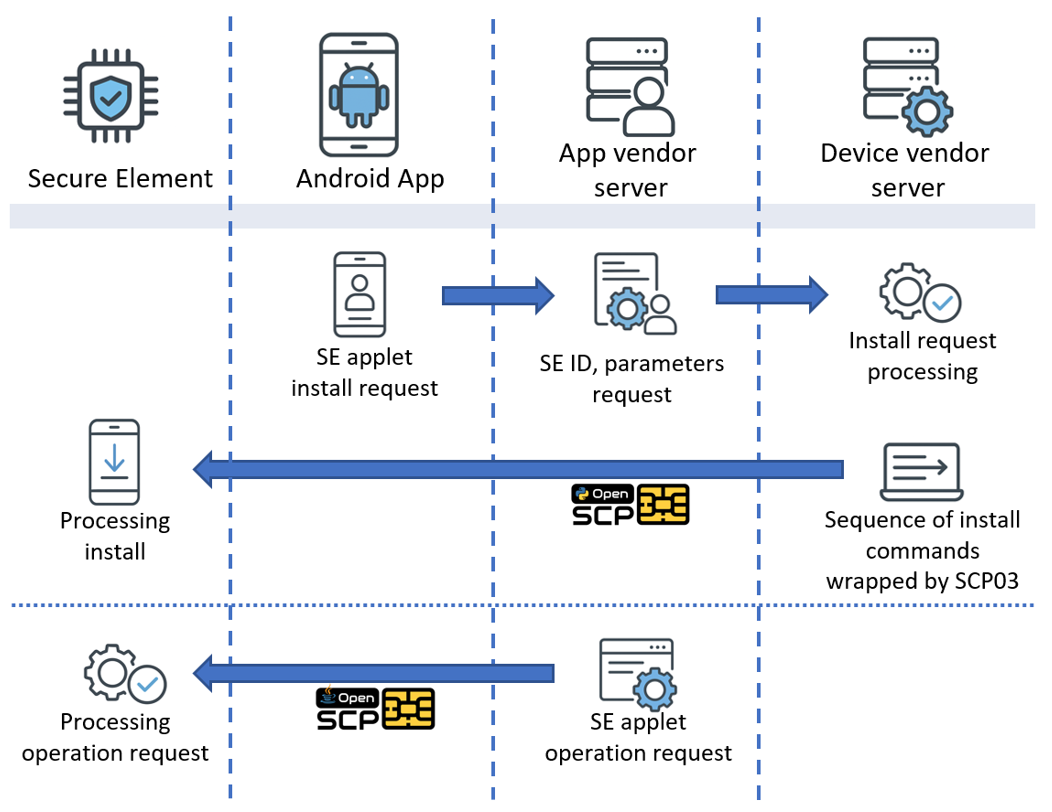
Figure 3. OpenSCP SCP03 operation for applet installation to SE and applet management
At Figure 3, to install a new Secure Element applet the following steps are taken:
SCP11
SCP11 protocol addresses the limitations of SCP03 by using asymmetric crypto (Elliptic Curve) for ephemeral key agreement and certificate-based authentication. SCP11 operation is similar to TLS. The major SCP11 features:
Figure 4 shows the scenario where Android Application or Application Vendor server communicates with SE applet to perform a business operation (like withdrawing trips from travel card). Android Application, Application Vendor server, and SE should be provisioned with SCP11 certificates at the Device Vendor infrastructure. Samsung OpenSCP [4][5] library is used here with Android Application and Application Vendor Server to establish secure communication channel.

Figure 4. typical setup of SCP11
SCP11 protocol has several modes that can be used in different commercial scenarios: SCP11a, SCP11b, SCP11c. All three use ECDH (elliptic curve Diffie-Hellman). They differ in what kind of authentication is used and what keys are static vs. ephemeral.
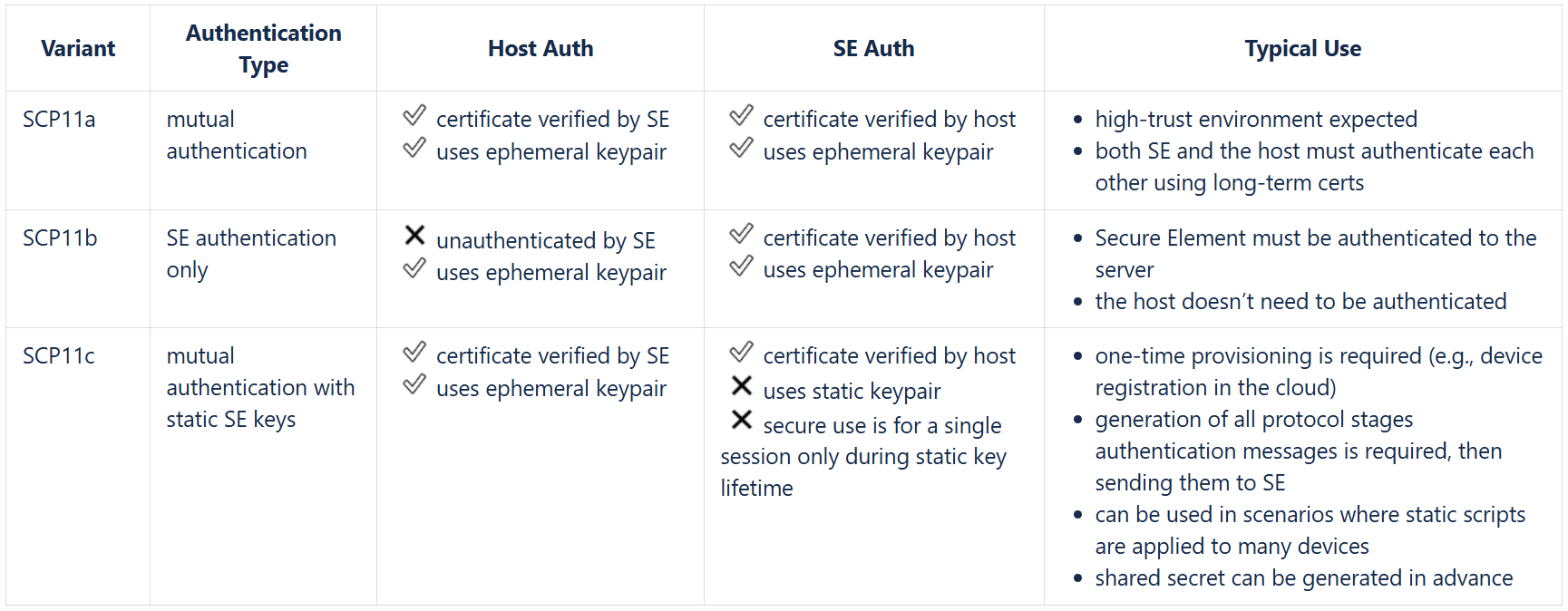
Table 2. SCP11 modes comparsion
Figure 5 shows mutual authentication according to SCP11 protocol
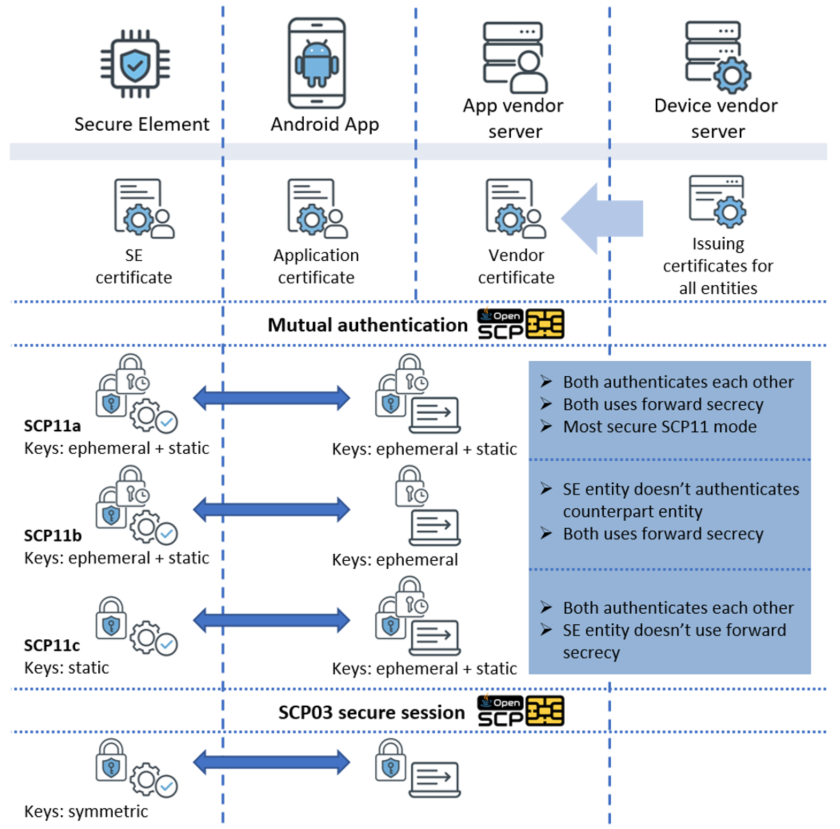
Figure 5. SCP11 protocol typical workflow for mutual authentication
SCP11 is scalable. It has more flexible security model than SCP03. It is suitable for SE-enabled constrained IoT and cloud-based settings.
Contribution is welcome
We welcome everyone’s feedback about OpenSCP. The project is also open for everyone willing to make source code contribution. Our partners dealing with eSE can use the code to speed up integration, improve security and compatibility. Future publications are planned to give more implementation details for potential open-source contributors to our OpenSCP library.
References
1. Wikipedia, "Secure element", Wikipedia, The Free Encyclopedia, 2025. [Online]. Available: https://en.wikipedia.org/wiki/Secure_element2. GlobalPlatform, Secure Channel Protocol '03' - Amendment D v1.2, 2025. [Online]. Available: https://globalplatform.org/specs-library/secure-channel-protocol-03-amendment-d-v1-2/
3. GlobalPlatform, Secure Channel Protocol '11' – Amendment F v1.4, 2025. [Online]. Available: https://globalplatform.org/specs-library/secure-channel-protocol-11-amendment-f/
4. Samsung, "OpenSCP-Java", GitHub Repository, 2025. [Online]. Available: https://github.com/Samsung/OpenSCP-Java
5. Samsung, "OpenSCP-Python", GitHub Repository, 2025. [Online]. Available: https://github.com/Samsung/OpenSCP-Python
6. GlobalPlatform, "GlobalPlatform Official Website", 2025. [Online]. Available: https://globalplatform.org/
7. GlobalPlatform, "Search results for ‘secure channel protocol’", 2025. [Online]. Available: https://globalplatform.org/?s=secure+channel+protocol
8. Wikipedia, "Evaluation Assurance Level", Wikipedia, The Free Encyclopedia, 2025. [Online]. Available: https://en.wikipedia.org/wiki/Evaluation_Assurance_Level
9. GlobalPlatform, Card Specification v2.3.1, 2025. [Online]. Available: https://globalplatform.org/specs-library/card-specification-v2-3-1/
10. International Organization for Standardization, "International Organization for Standardization Official Website", 2025. [Online]. Available: https://www.iso.org
11. International Organization for Standardization, ISO/IEC, 7816-4:2020 Identification cards — Integrated circuit cards. Part 4: Organization, security and commands for interchange, 2025. [Online]. Available: https://www.iso.org/standard/77180.html
12. Wikipedia, "Public key infrastructure", Wikipedia, The Free Encyclopedia, 2025. [Online]. Available: https://en.wikipedia.org/wiki/Public_key_infrastructure






